A
computer virus is a small
software
program that can spread from one computer system to another and cause
interferences with computer operations. A computer virus has the
capacity to corrupt or to delete data on your computer and it can use an
e-mail program to spread the virus to other email addresses in your
online address book. In the worst case scenario, it can even delete
everything on your hard disk.
Forms of Computer Viruses
In
the same way as viruses harm peoples' bodies, computer viruses can do
considerable damage to computer systems. Viruses are infections.
Computer infections can come in several forms and your computer can
"catch" one in several ways:
- An email virus
is one type of computer virus. An email virus can travel through
attachments in email messages and can automatically replicate itself by
mailing itself to dozens or even hundreds of people on your list of
contacts found in your online address book. There are email viruses that
can launch themselves into your computer while you are simply viewing
the messasge. You don’t even need to double-click the message in order
for the message to install itself.
- A Trojan horse
is not a virus. It is a computer program that claims to be a game but,
in actuality, will just do damage once you run it. It may even erase
your hard disk. It cannot automatically replicate itself.
- A worm
is a type of software called mallware that uses security holes and
computer networks in order to replicate itself. The worm will scan the
network for machines which carry a particular security hole. It will
then copy itself to the machine through the security hole and will start
replicating itself.
Viruses in general, start working and
spreading once you start using the application or program to which the
virus is attached. For instance, a program that has a virus in it will
place the virus in the system’s memory each time that program is run.
Once
the virus is in the memory, one of several things can happen. First, it
can be programmed to attach itself to other programs and applications,
folders, or disks. Second, if given the chance, it can infect a network.
How Computer Viruses Are Activated
Computer
viruses are easily spread through the use of attachments in various
email messages or via messages from instant messaging; so, you must
never open unexpected email attachments unless you know and trust
whoever sent the message.
Be very careful as computer viruses can
be easily disguised as ordinary-looking attachments or even as
attractive images, funny graphics, cards, video, and audio files.
Computer viruses can also spread through downloads you do while online.
They can be hidden in software, especially in
pirated items, or in other programs and files which you are downloading.
How Computer Viruses Operate
Viruses
operate in a multitude of ways. Some will stay active only when the
application to which it is attached is running. Others will be inactive
once the computer is turned off, while some will run every time you turn
your computer on after it has infected the network or system files.
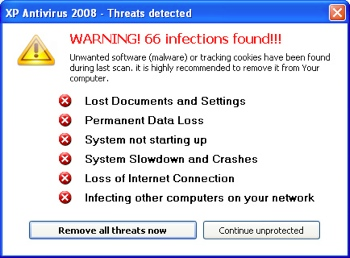
There are some indicators that will tell you that your computer is infected:
- Your computer is running slower than normal
- Computer applications are not working right
- Disk drivers and disks have become inaccessible
- You cannot print
- You find unusual, error messages
- Dialog boxes and menus are distorted
- You find double extensions on attachments which you’ve recently opened (ex. gif, jpg, vbs)
- Your antivirus program is suddenly disabled or cannot be restarted
- Antivirus programs cannot be installed in your computer or cannot run
- New and unusual icons suddenly appear on your desktop
- Strange music or sounds suddenly play from the speakers
- A program you typically use suddenly disappears from your computer without you purposely removing it
To
safeguard your files and to protect your computer, take time to
understand computer viruses and what you should avoid doing to save your
system from the virus. Be sure to always turn on the
firewall, keep your computer’s operating system updated, update your antivirus software, and use updated antispyware programs





























 The Print Screen key allows you to take a snapshot of everything
displayed on your laptop’s screen. You can use this feature to save
screen information as an image or create images for business documents,
websites or presentations. Some laptops require you to press and hold
the Function (Fn) key in order to use the Print Screen key to save the
screen capture. Once you’ve taken the screen capture, you can paste it
into a graphic program, such as Microsoft Paint, to convert it into an
image.
The Print Screen key allows you to take a snapshot of everything
displayed on your laptop’s screen. You can use this feature to save
screen information as an image or create images for business documents,
websites or presentations. Some laptops require you to press and hold
the Function (Fn) key in order to use the Print Screen key to save the
screen capture. Once you’ve taken the screen capture, you can paste it
into a graphic program, such as Microsoft Paint, to convert it into an
image.





